Sign macOS app
In order to deploy macOS privacy preferences policy via MDM/DEP, the macOS app in Mojave that needs exceptions must be signed. Otherwise, a user has to create exceptions to allow remote control via ConnectWise Control, which isn't ideal. I don't want to have to sign your app to get the payload pushed out to create the exceptions from our management software. If you signed your apps like other developers, this would be much easier for all users, like those of the Addigy and JAMF communities.





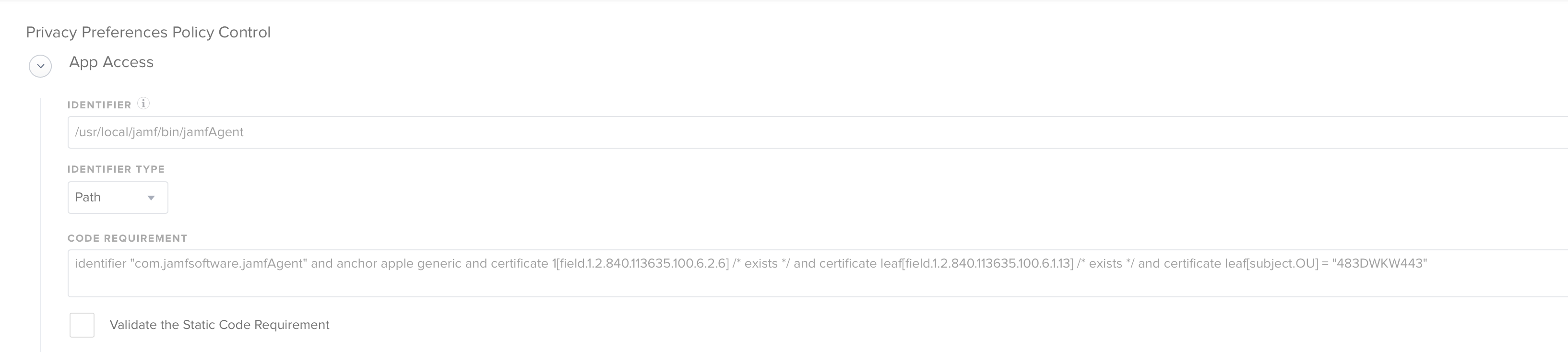
This has been an issue for some time and it is getting worse with the latest release of MACOS Mojave. https://control.product.connectwise.com/communities/6/topics/1974-complicated-process-required-to-control-macos-1014-mojave-clients
Security requirements are increasing and there may come a point where we cannot use ScreenConnect to manage/support Macs. If that happens, it will force us to abandon Screenconnect for managing Macs which means less revenue for you. Since you have a cert in use for the windows EXE, why not sign the PKG files for Macs with the same cert? Can someone in business development review this and get an internal count of how many hundreds or thousands or tens of thousands of machines are currently under Control? It's likely a big impact.
Thanks for your time and consideration.