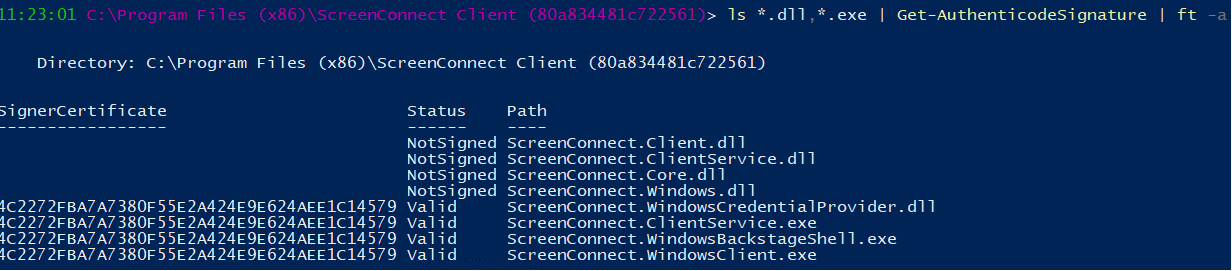
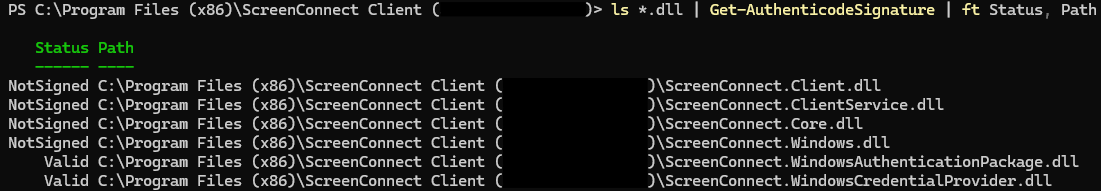
Code sign Connectwise Control .dll's
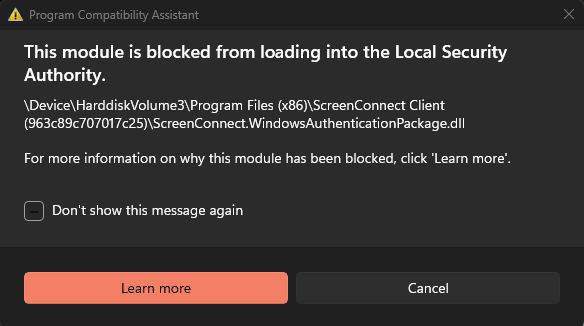
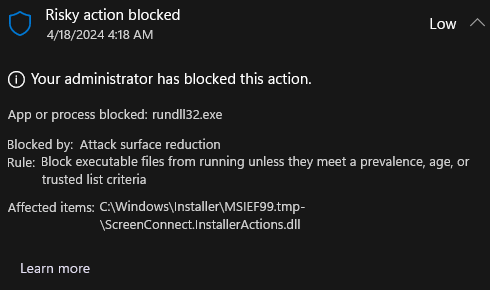
When a new version of the Screenconnect client is released & installed, Microsoft Defender for Endpoint - Attack Surface Reductions' rule "Block executable files from running unless they meet a prevalence, age, or trusted list criterion" denies the libraries from being used as they have no reputation.
This is expected behavior as a new version of the client being released globally is seen as "unknown" by Microsoft Security products.
The executables are not being flagged as low reputation as they are digitally signed & Microsoft have "established trust" with the code signing certificate in use.
Our request is to please sign the .dll's as well, without this digital signature, Microsoft wont "trust" the new files straight away which causes issues until enough devices globally have the client installed & Microsoft's systems learn / trust them.
It also enables us to create a trusted code signing certificate "Indicators", excluding any executable & dll from ASR rules etc, preventing these types of issues.
Support case reference #01401061



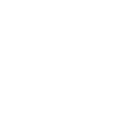


+1 please implement!