Restrict Administrator to access from Specific Networks
In an on-site implementation of ScreenConnect, we have setup multiple accounts all with 2-factor authentication. Likewise in order to protect the administrator account specifically or what it is renamed to, we would like to allow the account to remain in the event 2-factor failures occur, without triggering a full product reset of the "issetup" flag. Thus, is there a way easily to isolate the specific users or user group like the "Administrator" privileges provide to only being allowed to log in from a specific local area network, or trusted networks per say.




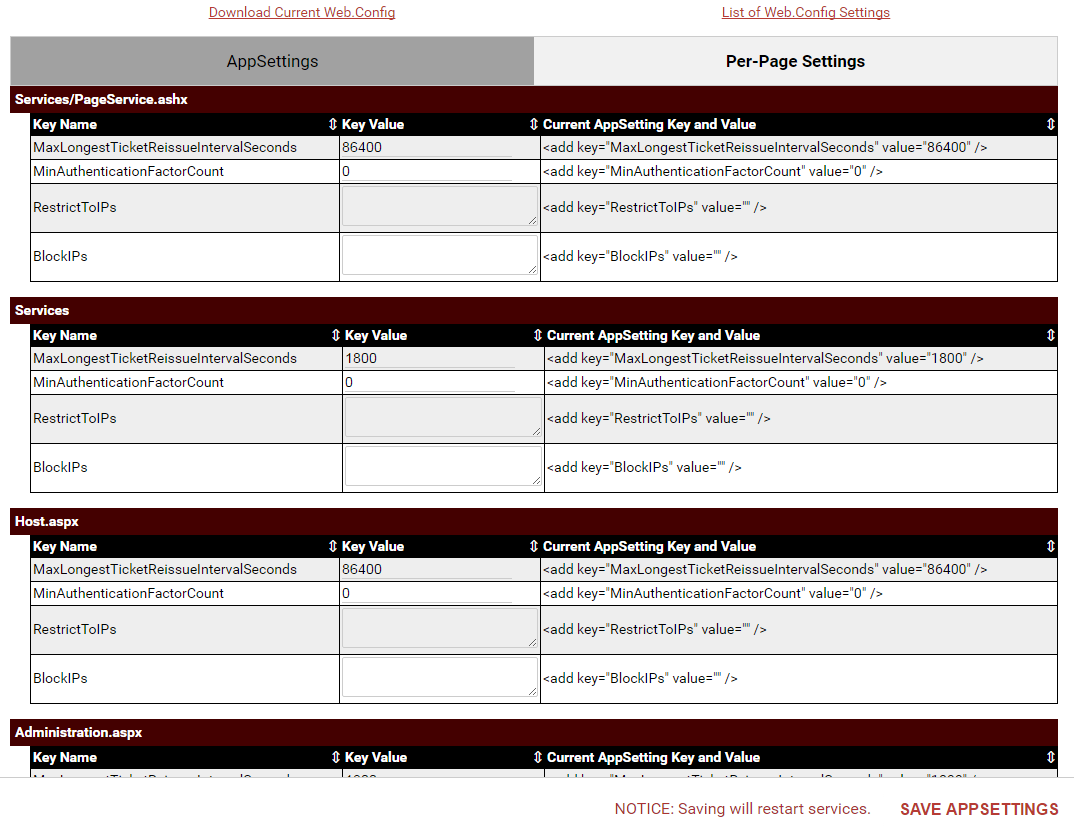




I would like the ability to force techs to be on a certain IP network.. Guests may be from any IP network.. But.. Techs have to be on our private LAN for example (192.168.1.0/24) to be able to log in as a tech.. This forces techs to be either on our LAN or in a VPN.