Support ALL Duo 2FA authentication methods
The addition of Duo push 2FA is great but a bit puzzling. Why only support push when Duo supports so many authentication options and they make it easy to implement them all.
- Some people don't have a smartphone where they can install the Duo app so push won't work for them but they can still receive a text message of phone call just fine. Duo supports both of these options for 2FA but
Screenconnect'sControl's integration was is implemented in a way that does not allow them. - Some people might have multiple devices with the Duo app installed and need to choose which one they want the push sent to. Duo allows users to choose which one they want to receive a push from, or which one they want to receive a text or call on. Again Control's integration does not allow this.
- Ever forgotten your mobile phone at home? I have and that's why I've configured my Duo account with a hardware token too. Unfortunately Control's integration does not support this Duo 2FA method either.
- Perhaps you are prone to forgetting your mobile device but don't want to have a hardware token. In this case Duo can be configured with bypass code (basically a OTP that you know beforehand). Well, you know the story.
I'd really like to see Control support the all the Duo authentication methods and for the looks of their documentation this should be relatively easy.
https://duo.com/docs/duowebAs an added bonus this also provides a natural way to handle the 2FA logon rather then show the user a prompt for a code that they can't type (what your Duo 2FA currently does).
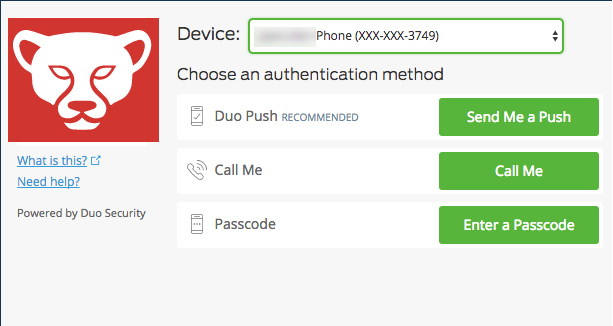









The current DUO integration is very hacked together. Having DUO integrated properly so that it is easy to connect and all of DUO's connect methods are supported. The login page should also automatically continue after a push is initiated without having to press the login button (almost all DUO integrations work this way).