Set up SAML with Azure AD as enterprise application
As of October 15 this year, Azure AD no longer accepts domains that the tenant doesn't manage themselves in their App ID URI field when setting up a custom SAML app, domains like screenconnect.com
This makes sense, I suppose, because custom SAML apps are for those trying to integrate apps that they built themselves or at least manage the DNS records for.
Anyway, this new development means that ConnectWise in fact no longer supports SAML integration with Azure AD / Microsoft 365.
The issue has been registered as #SCP-37400 on ConnectWise Home, but I think the way forward is clear — ConnectWise should register Control as an enterprise app on Azure AD, like Splashtop and Teamviewer have done. That's why those solutions haven't been affected by this new policy by Azure AD.
Registering as an enterprise app would be ideal, as this would make the set up process for SAML integration much easier as well.



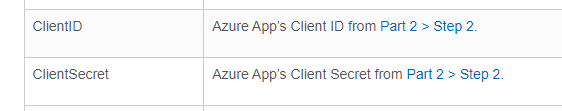



This is what's posted on ConnectWise Home.
The Microsoft docs link is to this page.
No solution is offered, but as I wrote above, registering as an enterprise app seems to be the best (only?) way.